How I Boosted AWS Security and Efficiency with Multi-Account Management Using AWS Control Tower
When I first started managing multiple AWS accounts, I thought AWS Organizations was the ultimate tool for the job. It helped me organize accounts into logical groups and apply service control policies, but I quickly realized it wasn’t enough. Ensuring security, compliance, and scalability across dozens of accounts still felt like a never-ending battle—until I discovered AWS Control Tower. In this post, I’ll share how Control Tower transformed my approach to multi-account management and why it’s a must-use tool for cloud security and efficiency.
What is AWS Control Tower?
AWS Control Tower is a fully managed service designed to simplify the setup and governance of a secure, multi-account AWS environment. It provides a centralized dashboard, automated compliance checks, and pre-packaged governance rules, ensuring that security is never compromised.
What Makes AWS Control Tower a Game-Changer?
AWS Control Tower is more than just a tool—it’s a framework designed to simplify multi-account management while enforcing best practices. Here’s why it stood out to me:
1: Automated Setup:
- Control Tower automates the creation of a Landing Zone, including a Management Account, Log Archive Account, and Audit Account.
2: Built-In Guardrails:
- It comes with pre-configured guardrails that enforce security and compliance policies, such as restricting public access to S3 buckets.
3: Centralized Governance:
- Manage identity, access, and compliance across multiple accounts from a single place.
4: Simplified Compliance:
- Integrates with AWS Config and CloudTrail for continuous monitoring and auditing.
5: Shared Services Made Easy:
- Setting up shared resources like VPCs across accounts is seamless.
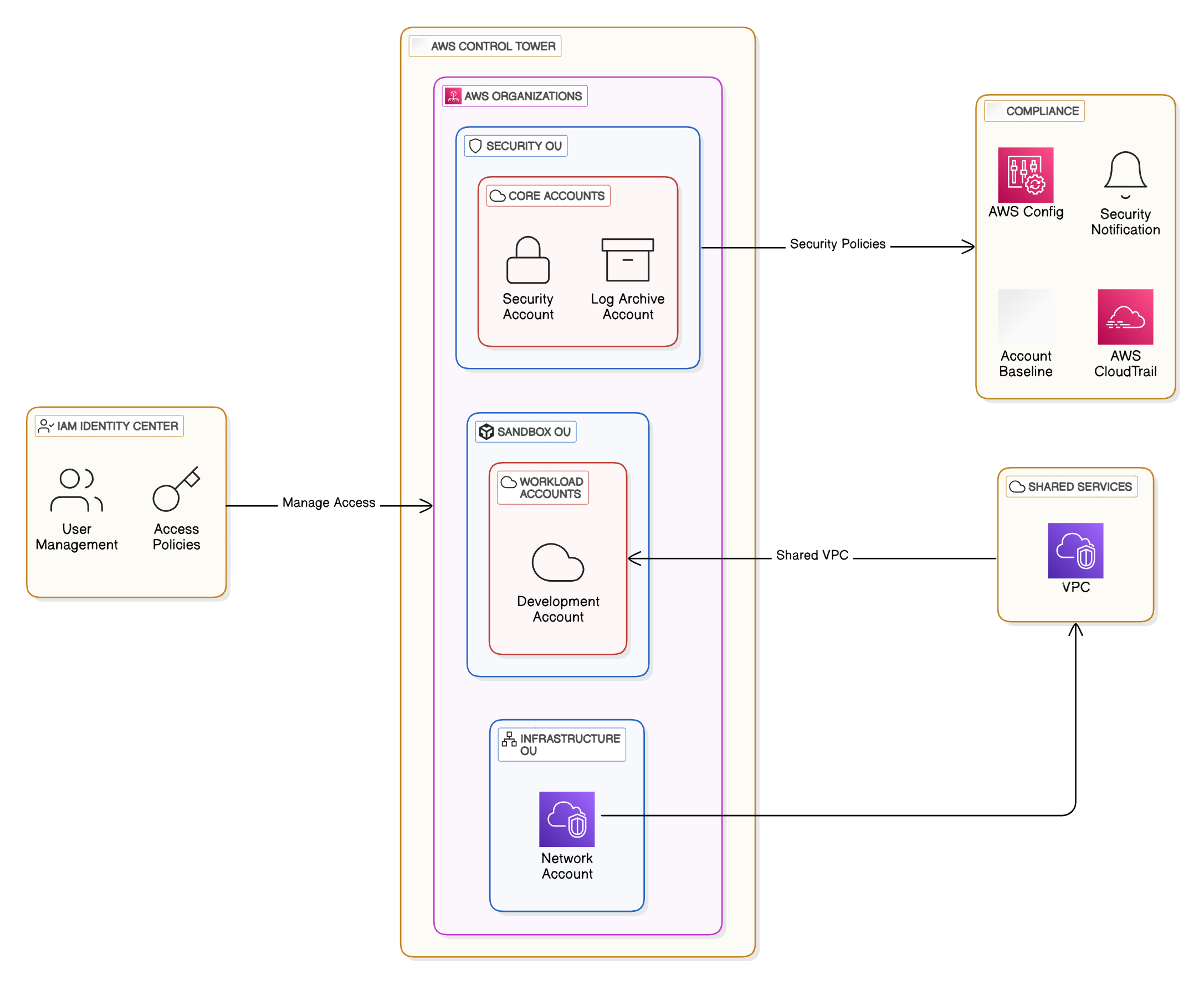
How I Built a Secure and Scalable Environment with Control Tower
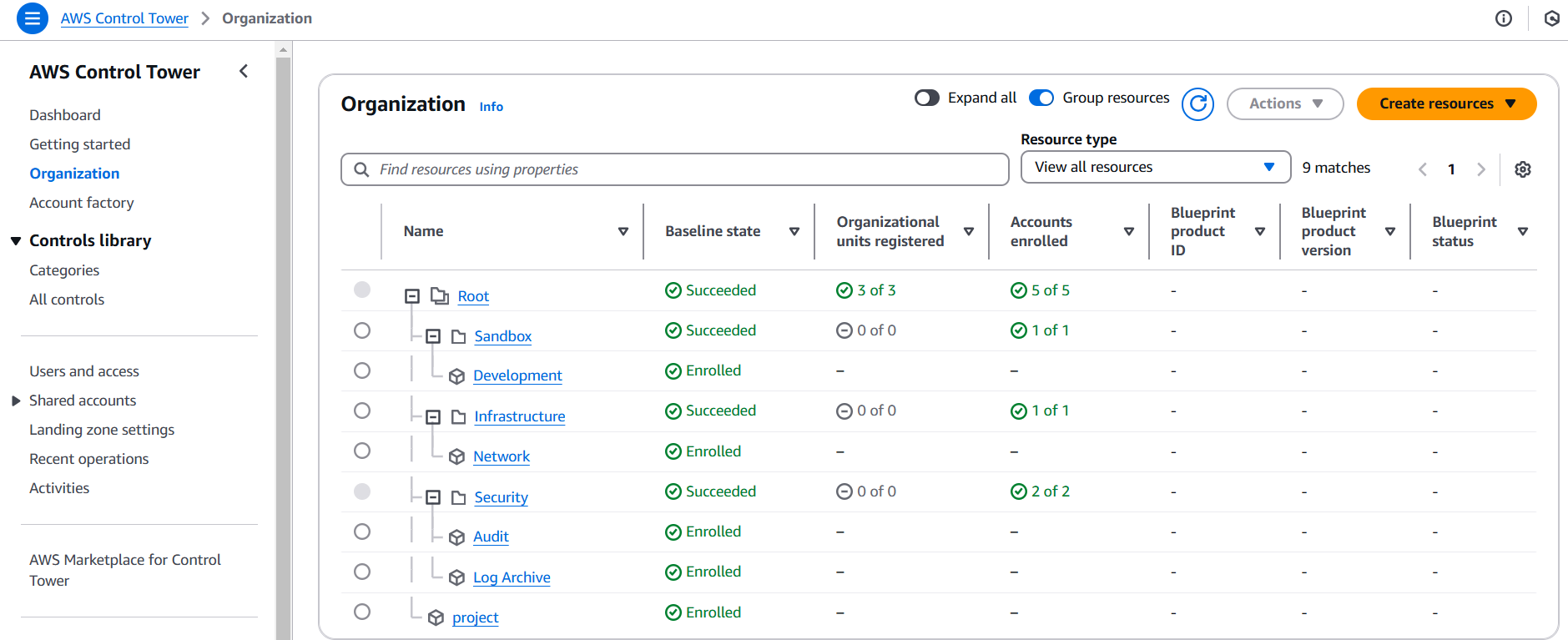
1: Landing Zones: The Foundation of Control Tower
The first step was setting up Landing Zones. This created a clean, hierarchical structure for managing accounts. Here’s what I did:
- Configured dedicated email aliases for the Log Archive and Audit accounts.
- Established a Management Account to oversee everything.
This structure helped me understand how to manage accounts and ensured clear boundaries between workloads.

2: Organizational Units (OUs): Structuring My Environment I organized the environment into two primary Organizational Units (OUs):
- Security OU: For core accounts like the Security Account and Log Archive Account.
- Sandbox OU: For Workload Accounts like the Development Account.
This setup taught me how to ensure proper workload segregation, which is critical for security and compliance.
3: Security Controls: Peace of Mind Built-In One of the standout features of AWS Control Tower is its built-in security controls. Here’s what Control Tower automatically set up:
- 20 Preventive Controls: These enforce policies across accounts, such as restricting public access to S3 buckets.
- 3 Detective Controls: These monitor and identify configuration violations.
These controls gave me peace of mind, knowing that my environment was secure and compliant—without me having to manually configure them.
4: Development Account: A Safe Space for Testing I created a dedicated Development Account within the Sandbox OU. This provided an isolated environment for testing and experimentation without compromising security.
5: AWS IAM Identity Center: Centralized Access Management

The AWS IAM Identity Center (formerly AWS Single Sign-On) is a key component of Control Tower. It simplifies identity management and provides a centralized Access Portal for users to securely access AWS accounts and applications. Here’s how I used it:
AWS Access Portal:
- Users can log in to the portal and access their assigned AWS accounts and applications.
- The portal allows filtering accounts by name, ID, or email address, making it easy to manage access across multiple accounts.
- For example, I assigned roles like AWSAdministratorAccess and AWSOrganizationFullAccess to specific users, ensuring they had the right level of access.
This centralized approach streamlined access management and improved security across my multi-account environment.
6: Automation: Saving Time and Money
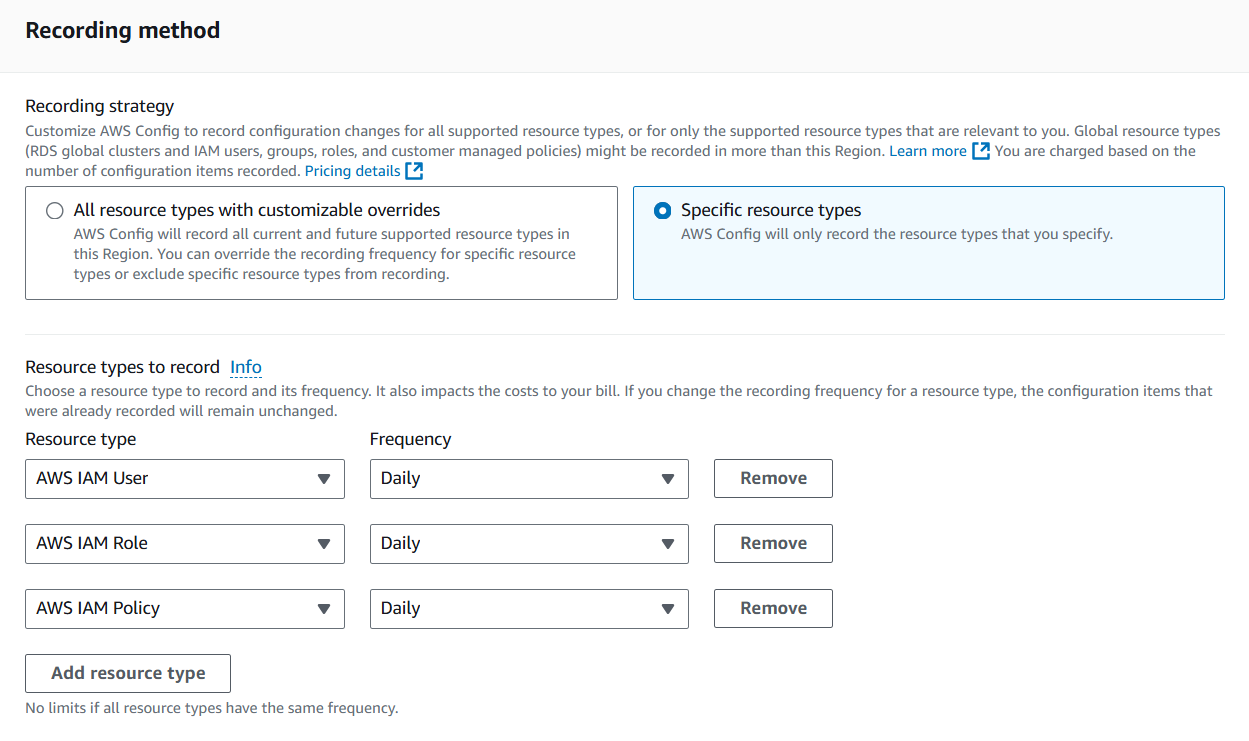
To optimize costs and streamline operations, I used a script that automates the configuration of AWS Config across all accounts in my AWS environment. The script ensures that AWS Config tracks only IAM resources (users, roles, and policies) and updates its recordings daily, significantly reducing costs while maintaining essential security monitoring.
Here’s what the script does:
1: Assumes the AWSControlTowerExecution Role: It assumes the AWSControlTowerExecution role in all accounts except the management account.
2: Updates AWS Config Settings: It configures AWS Config to:
- Track only IAM resources.
- Set the recording frequency to daily.
3: Reduces Costs: By narrowing the scope and frequency of monitoring, the script minimizes AWS Config costs while still providing critical visibility into IAM changes.
This automation has been a game-changer, saving both time and money while ensuring my multi-account environment remains secure and compliant.
Roadblocks and Solutions
While setting up AWS Control Tower and managing multi-account environments, I ran into a few hurdles. Here are two of the main challenges I faced and how I tackled them:
1: EC2 APIs Not Fully Enabled When I tried setting up Control Tower in a new account, it failed because the EC2 APIs weren’t fully enabled. This often happens with new accounts that haven’t completed their verification process.
What I Did:
- Launched an EC2 instance (t2.micro) in the same region where I was setting up Control Tower.
- Let the instance run for 30 minutes to allow AWS to complete the account verification process.
- Retried the Control Tower setup, which worked this time. Afterward, I terminated the EC2 instance.
2: Account Factory Enrollment Failures Enrolling accounts into the Account Factory sometimes failed due to issues like incorrect email addresses or hitting service quotas.
What I Did:
- Double-checked all email addresses to ensure they were correct and unique.
- Verified that the required IAM roles were properly configured.
- Checked for service quota limits (e.g., VPCs, IAM roles) and requested increases where necessary.
Key Takeaways
By exploring Control Tower, Landing Zones, OUs, and IAM Identity Center, I gained a deeper understanding of:
- Centralized Management: How to manage permissions and configurations across multiple accounts.
- Enhanced Security: The importance of built-in guardrails and detective controls.
- Streamlined Compliance: How continuous monitoring with AWS Config and CloudTrail works.
- Cost Savings: How automation can help identify and eliminate unnecessary costs.
- Scalability: How to design an environment that’s ready to grow.
Conclusion
AWS Control Tower is more than just a management tool; it’s a comprehensive solution that addresses the challenges of multi-account AWS environments. By automating the setup process and enforcing governance across accounts, it allows organizations to focus on what they do best — innovate and grow.
Whether you’re a large enterprise or a small startup, AWS Control Tower can simplify your cloud journey and ensure that you’re always operating within the bounds of security and compliance. Start your journey with AWS Control Tower today and take control of your cloud environment.